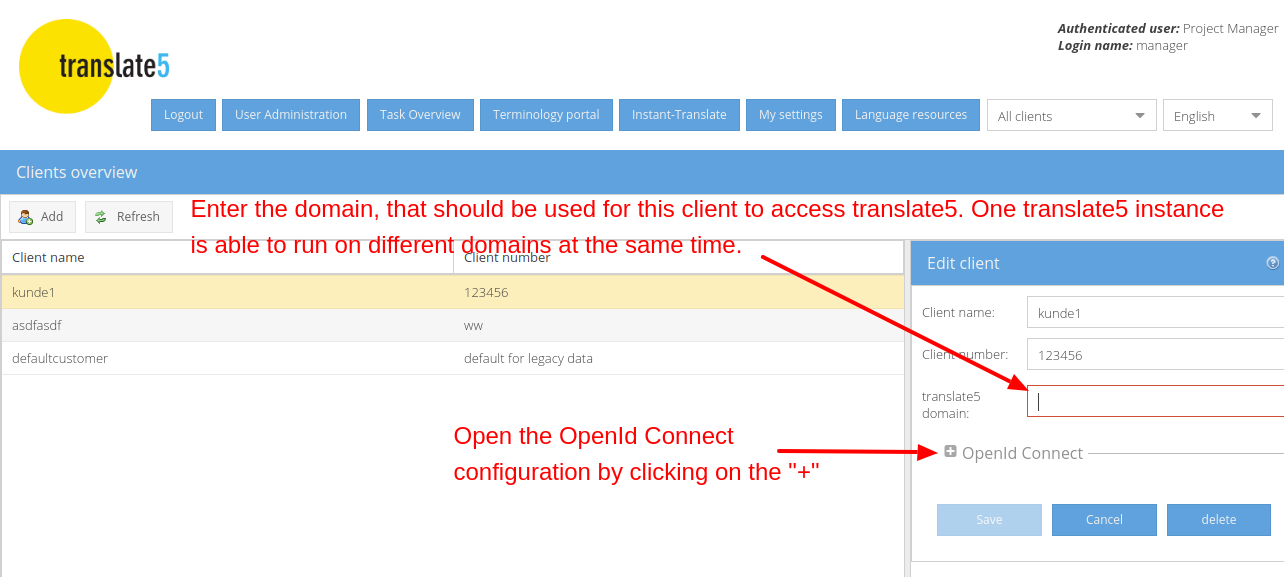
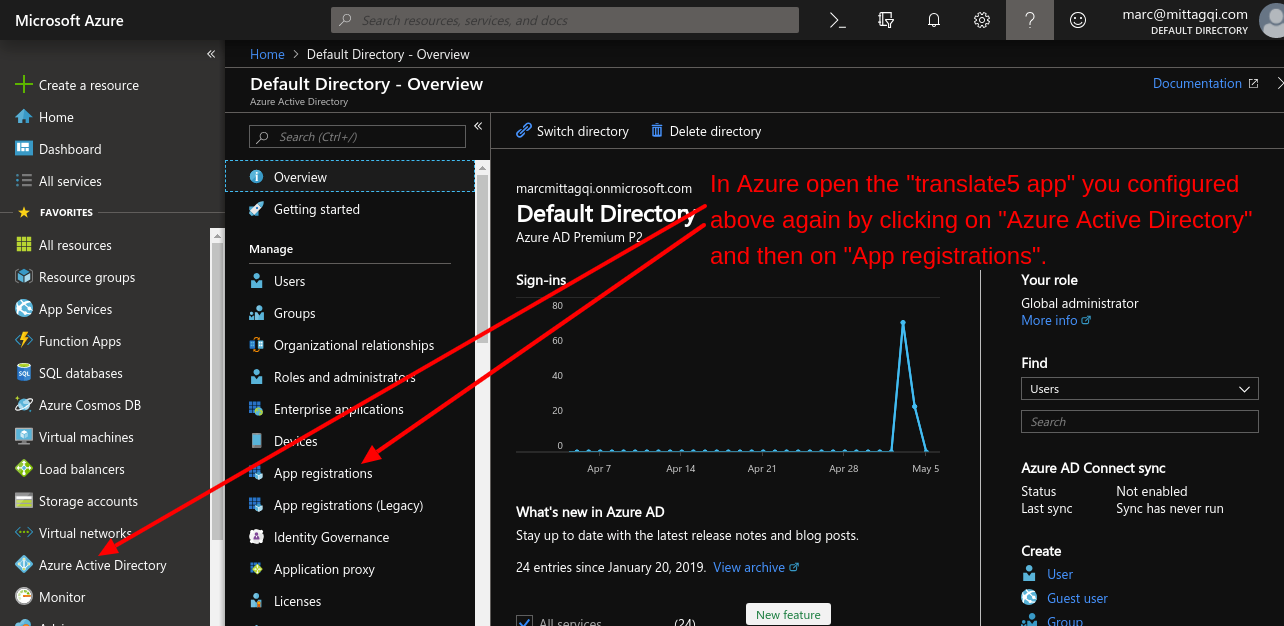
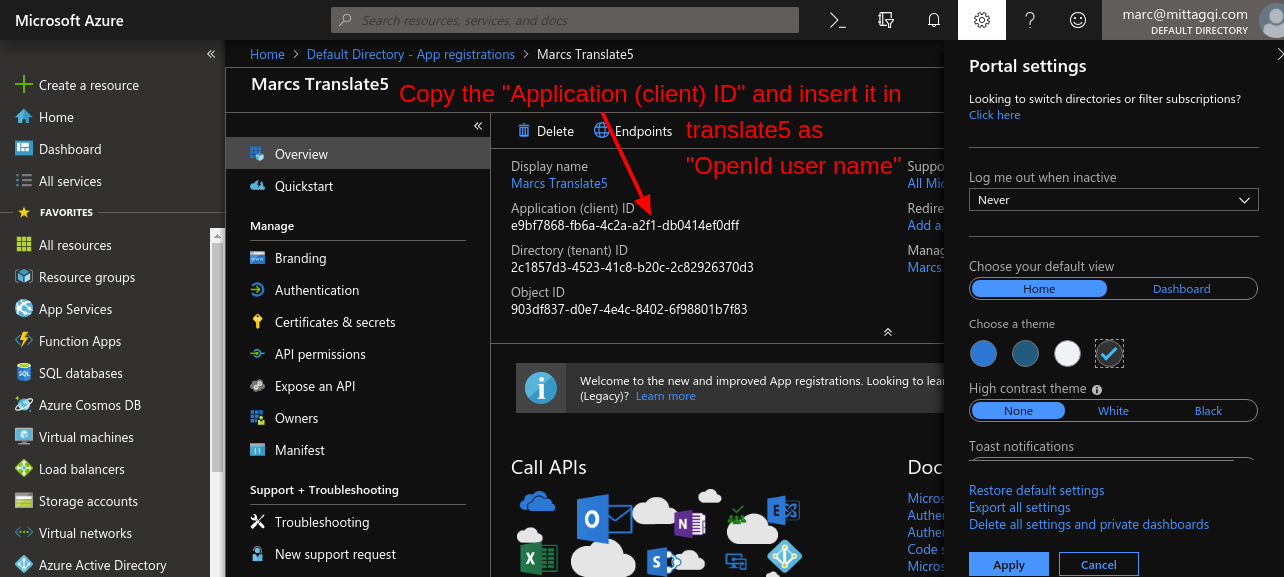
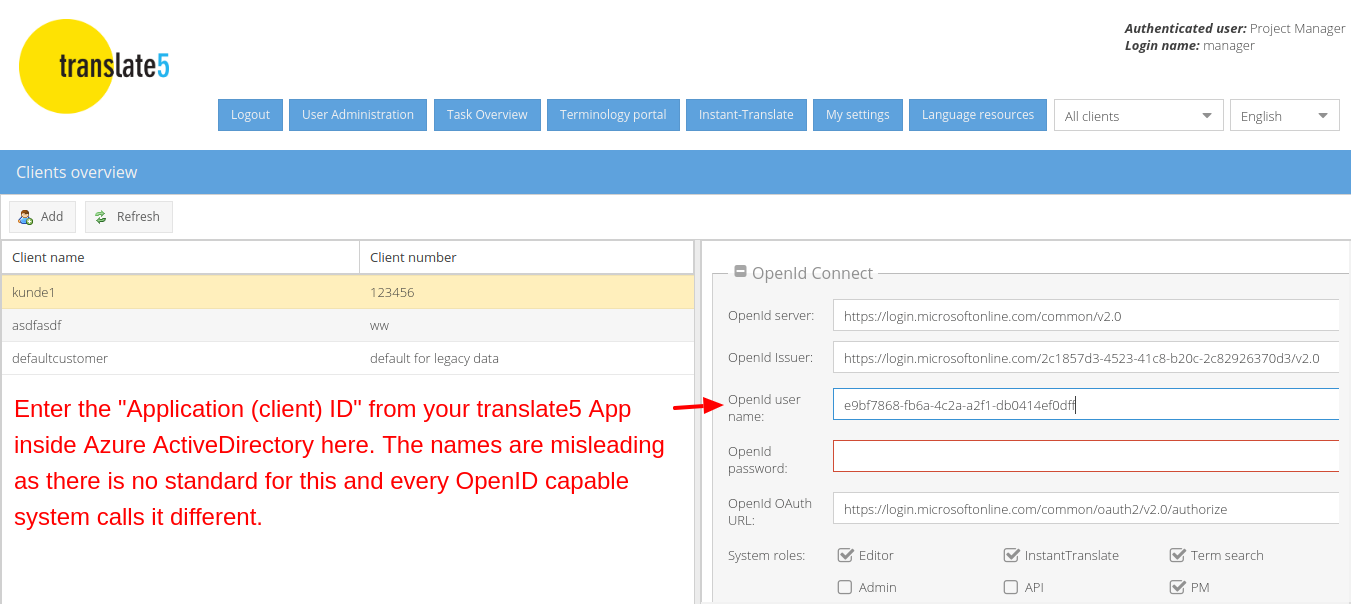
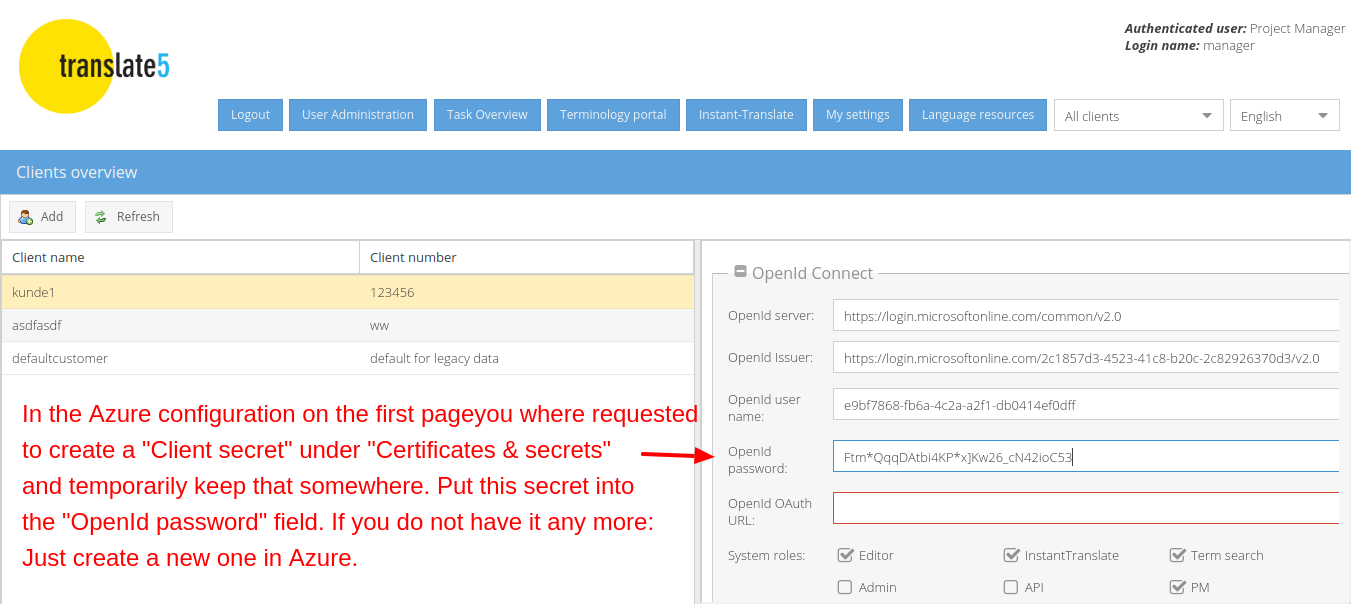
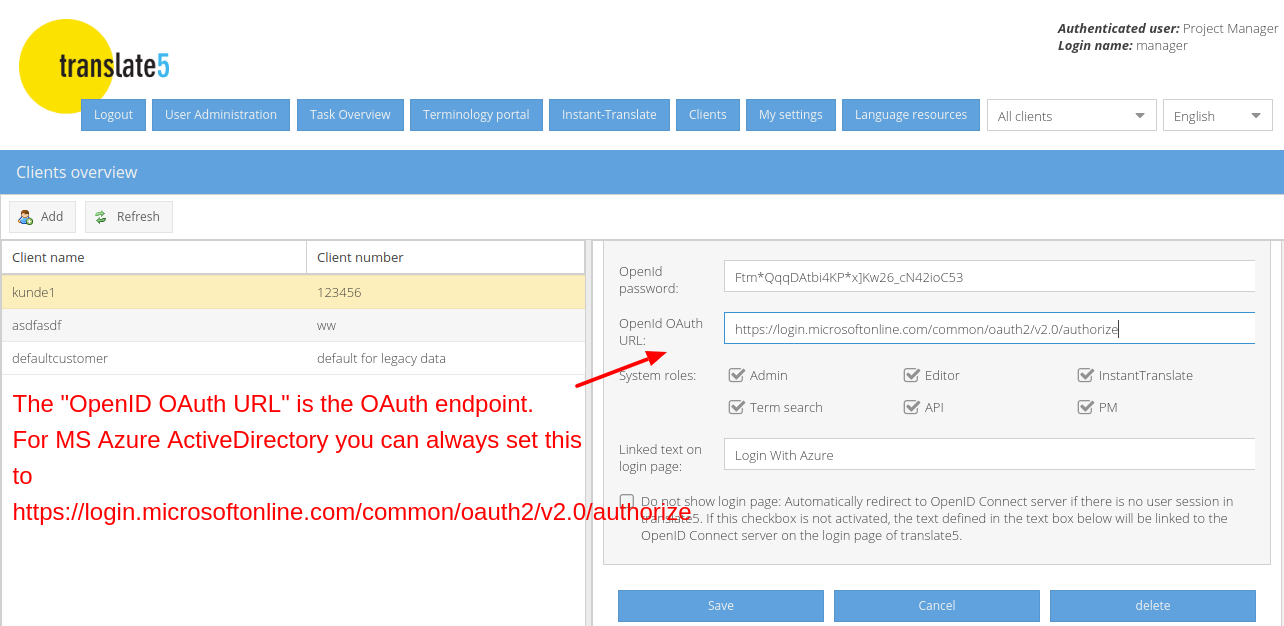
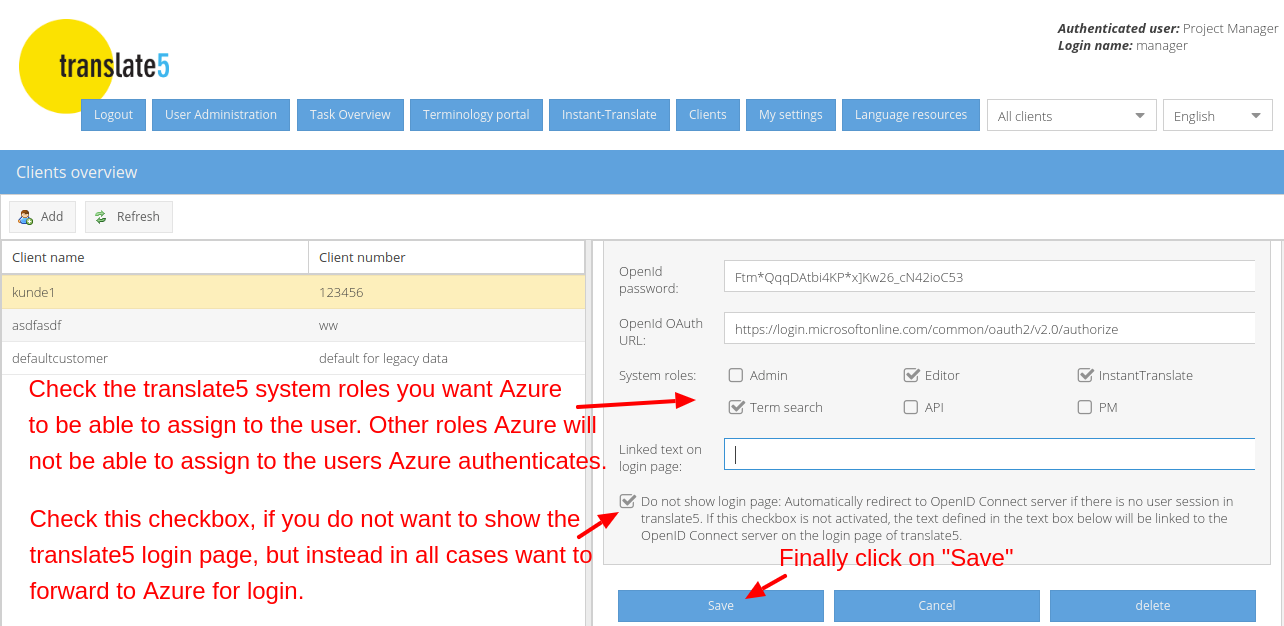
The following instructions show translate5 settings that are needed to use translate5 as OpenID connect client together with MS Azure ActiveDirectoy in conjunction with the Azure settings, that have been outlined above.
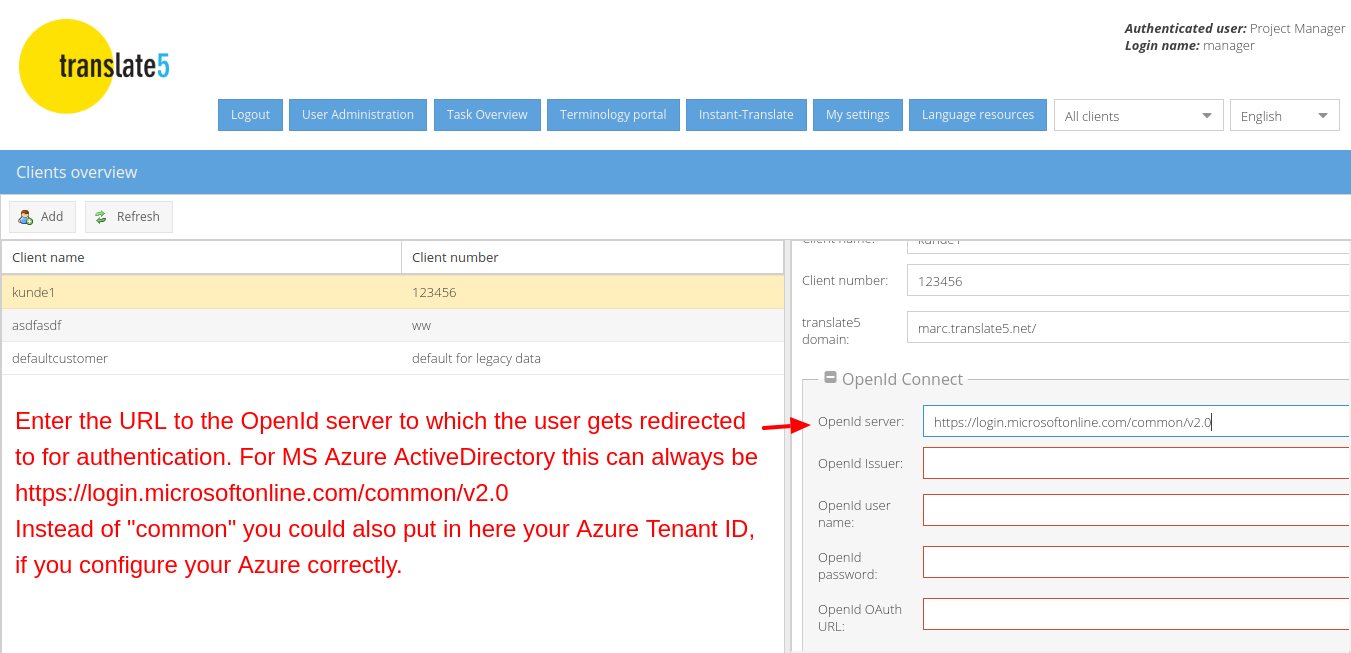
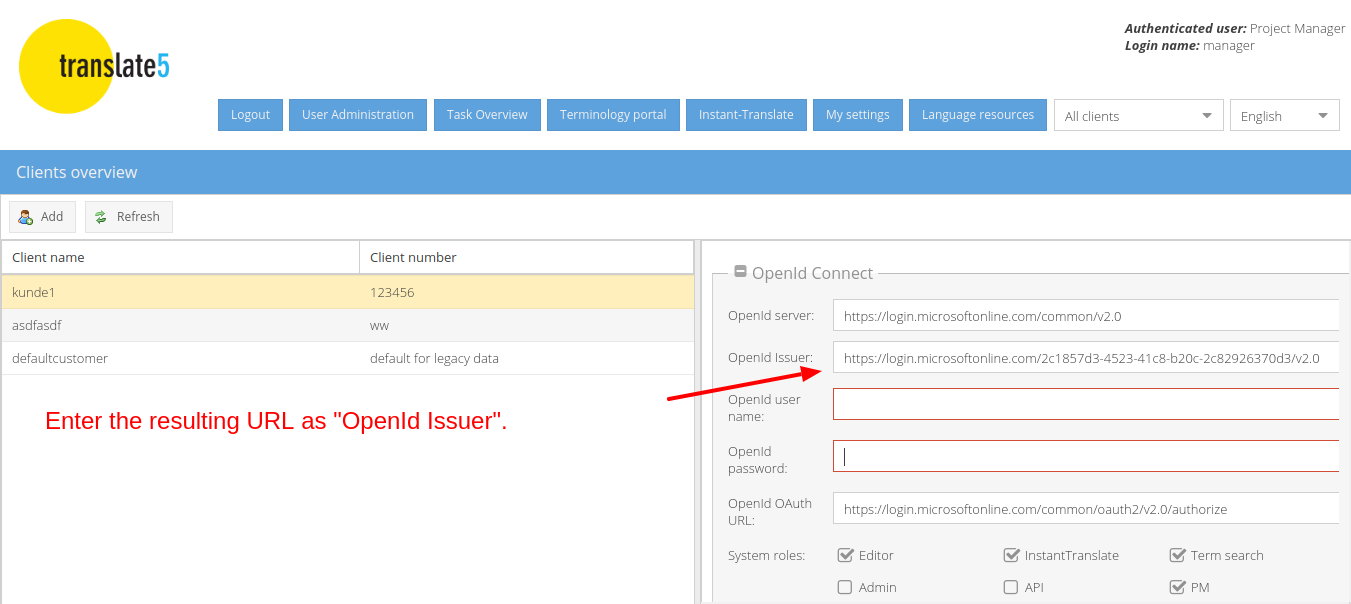
For convenience: Please find the MS Azure Login URL for the "OpenID server URL" field of translate5 below for copying:
https://login.microsoftonline.com/common/v2.0
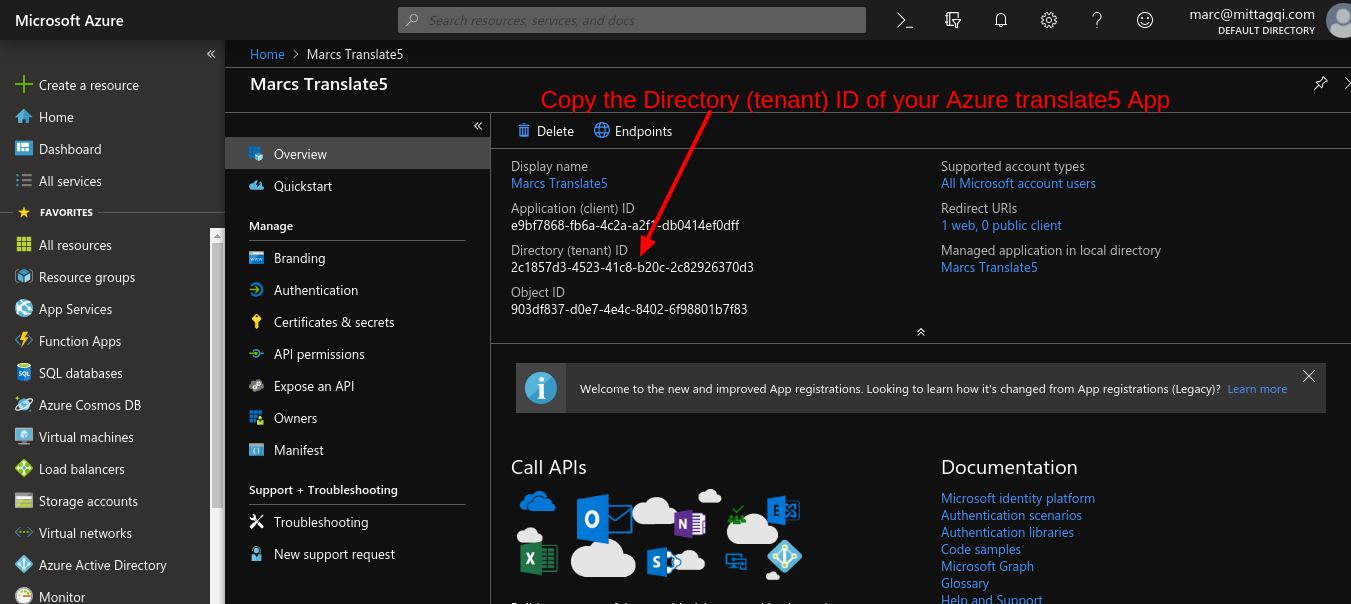
Combine the following URL template of the OpenId issuer URL with the "Directory (tenant) ID" from Azure
https://login.microsoftonline.com/{tenant-ID}/v2.0
by replacing {tenant-ID} with the ID you just copied from your Azure instance.
In my example the URL after replacing looks like this:
https://login.microsoftonline.com/2c1857d3-4523-41c8-b20c-2c82926370d3/v2.0
For convenience: Please find the MS Azure OAuth endpoint URL for copying in the following field:
https://login.microsoftonline.com/common/oauth2/v2.0/authorize
Congratulations - you are good to go now! Your users are able to sign in via Azure.
One important note: Since by default a gender is not specified in Active Directory, all users that are created via Azure Active Directory in translate5 will be female. If you do not want that, you have to create a custom user attribute for your Active Directory users and assign that as a claim to your translate5 app within Active Directory in the way showed in the Azure Active Directory optional claims configuration.
A second note: If you checked the last checkbox above, users are ONLY able to sign in via Azure on the domain, you defined for this client in its client configuration. On other domains of the same translate5 instance users will still be able to sign in via the login page.